The Verizon 2019 Data Breach Investigations Report finds phishing shows no signs of slowing down. In 2018, phishing efforts increased by 40.9%, showing cyber scammers are sticking with what works and they’re getting better at it. Stealing valuable data and company funds are two goals bad actors look to exploit. Organizations are particularly vulnerable to phishing because of continuing efforts by cybercriminals to get access to their employees and systems. Employees have become the first line of defense for an organization as they are the primary targets of phishing. Ongoing cyber education proves the best defense against phishing of all types, and reviewing the most common types and their warning signs goes a long way toward spotting the tricks of a fraudster’s trade. Just remember the first rule to combat phishing: If you’re not expecting it, don’t click it. Following are some other tidbits for keeping in the know.
Email Phishing “Fake Outs”
Fraudsters strive to make an email look legitimate. It includes subject lines and content having a sense of urgency or threat that the recipient mistakenly believes they must act on immediately for the good of their job. Whether it’s fake invoices needing to be paid, links redirecting users to real-looking but fake websites designed to steal important data, or malware-filled attachments are par for the course. The most common email phishing signs to lookout for are generic greetings and senders, spelling, and grammatical errors.
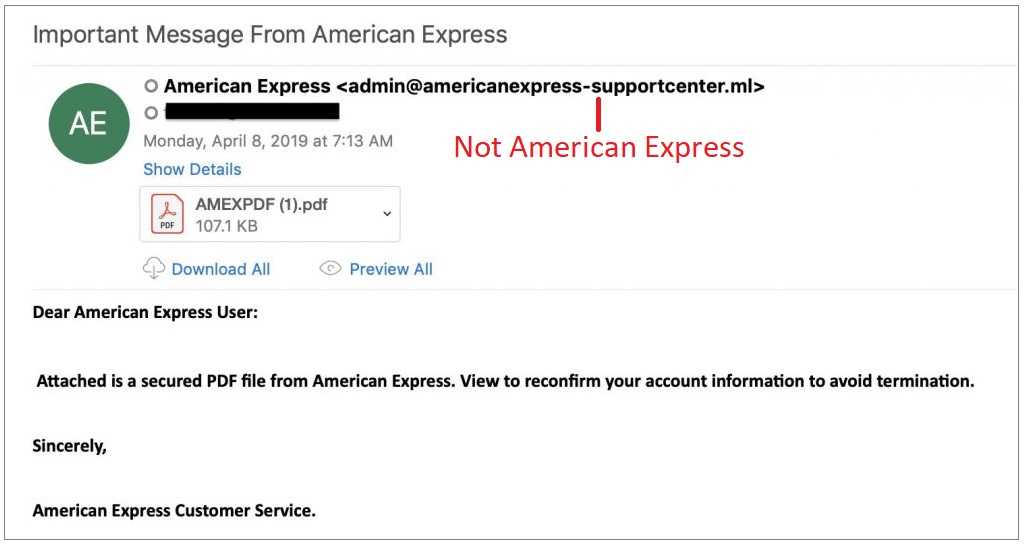
Spear Phishing Gets Personal
These schemes use information about an employee that targets them directly. It brings deception to a whole new level by capitalizing on an employee’s job title and contacts, personal information, or interests. Scammers easily glean information from social media and other sites, including the official company website. From there, hackers craft phishing efforts that capitalize on what they’ve learned about the recipient. Keeping exploitable information off public postings is something all organizations need to do. Employee training is a fraudster's worst enemy and an organization’s biggest defender. The most common spear phishing signs are messages from a recognized and trusted sender, especially those using personalized information.
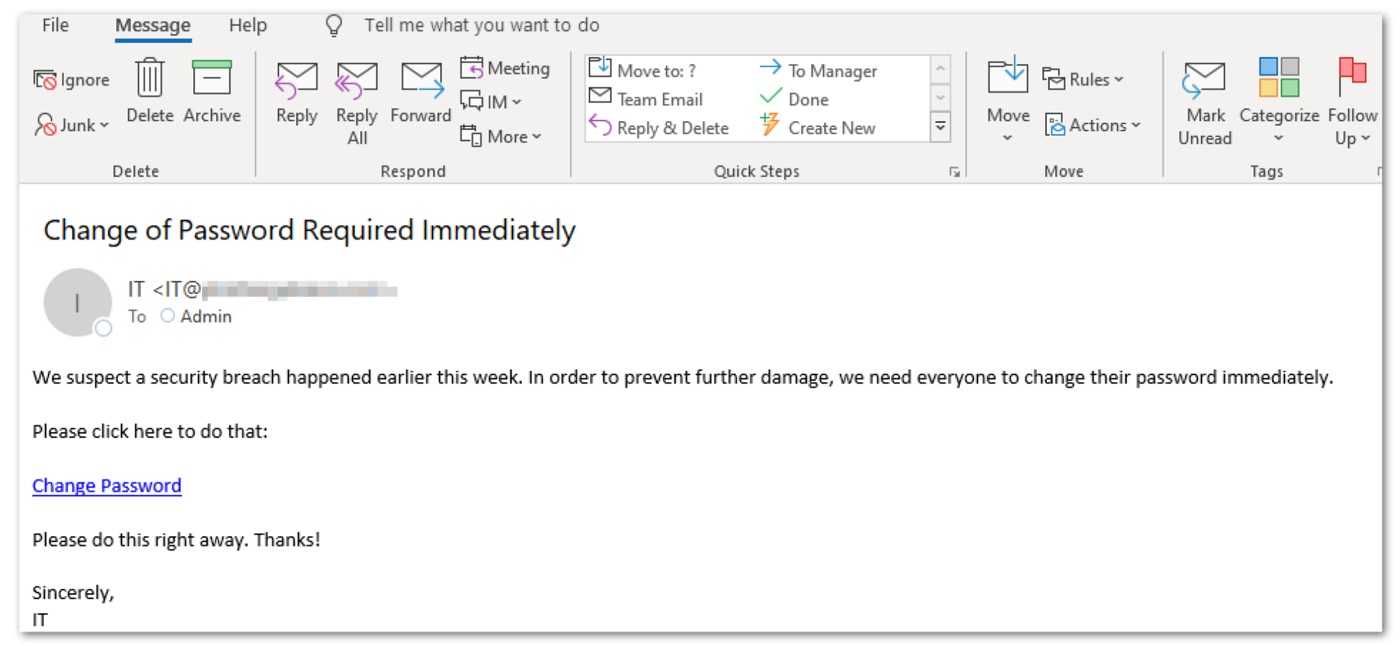
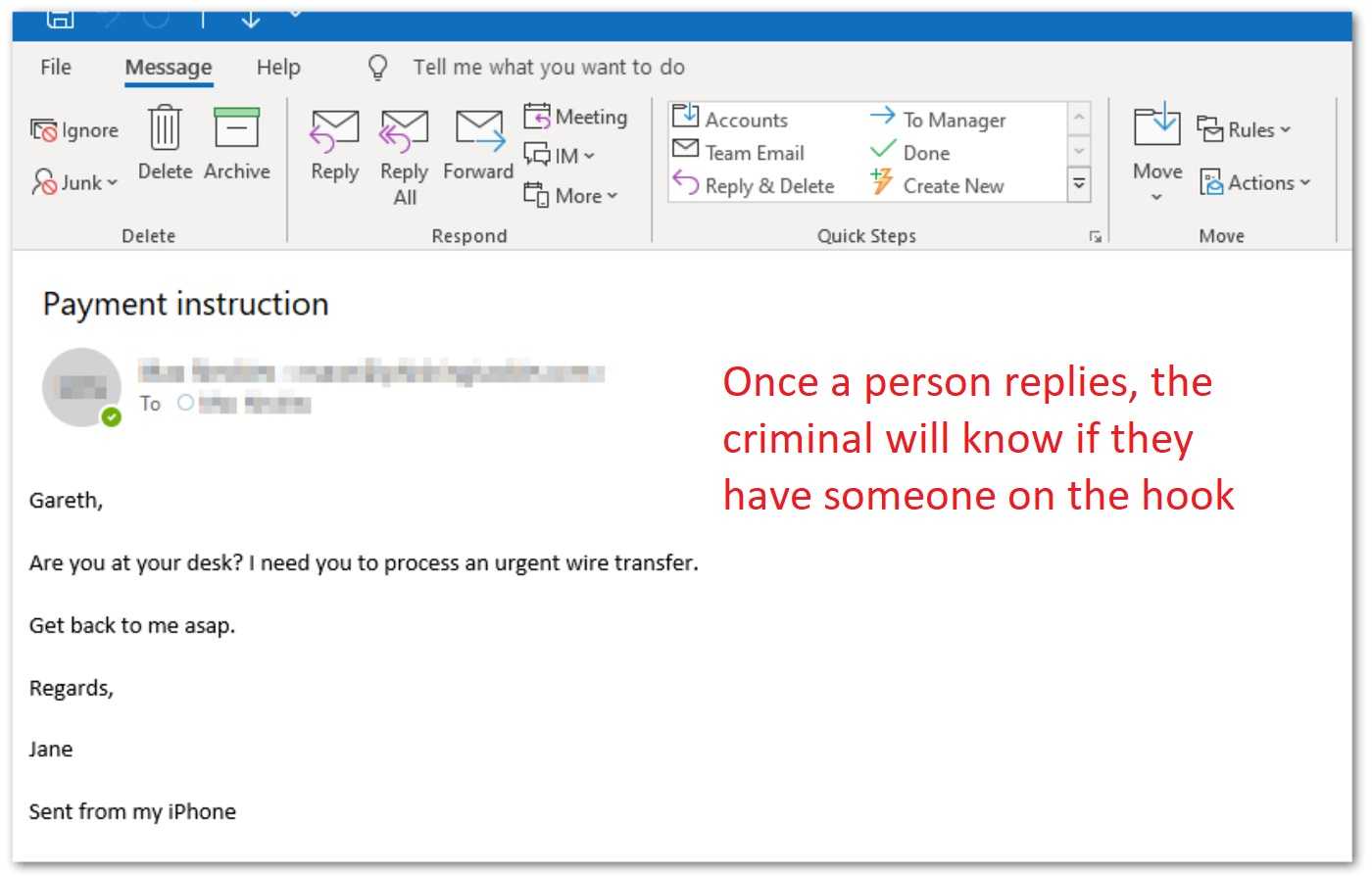
Whale Phishing for CEO’s
When a message comes from a high-ranking member of an organization or “whale,” employees and vendors take notice. Company executives are targets too and when a hacker compromises their login details, they are likely none-the-wiser. From there, business email compromise is easy to commit when a hacker can approve wire transfers to their own accounts by using a whale’s sensitive data. Cyber education for employees is vital, but big phish also need to be included in training. Multi-factor authentication (MFA) and multiple layer of approvals for wire transfers also go a long way to prevent whale phishing efforts.
Vishing Attacks: Say what?
Phishing efforts aren’t limited to email alone. Phone calls or “vishing” are another trick of the hacker trade that involves fooling the call recipient into believing the caller is legitimate. Bad actors can use Voice over Internet Protocol (VoIP) to mimic their authenticity and request sensitive data. Just some of the ploys may be appearing to be from the IRS or other authorities and are designed to steal sensitive data with a phone call. Remember, never give personal or sensitive information over the phone and when in doubt, hang up. You can always find the true known number of who claims to be calling and find out for real if your information is needed.
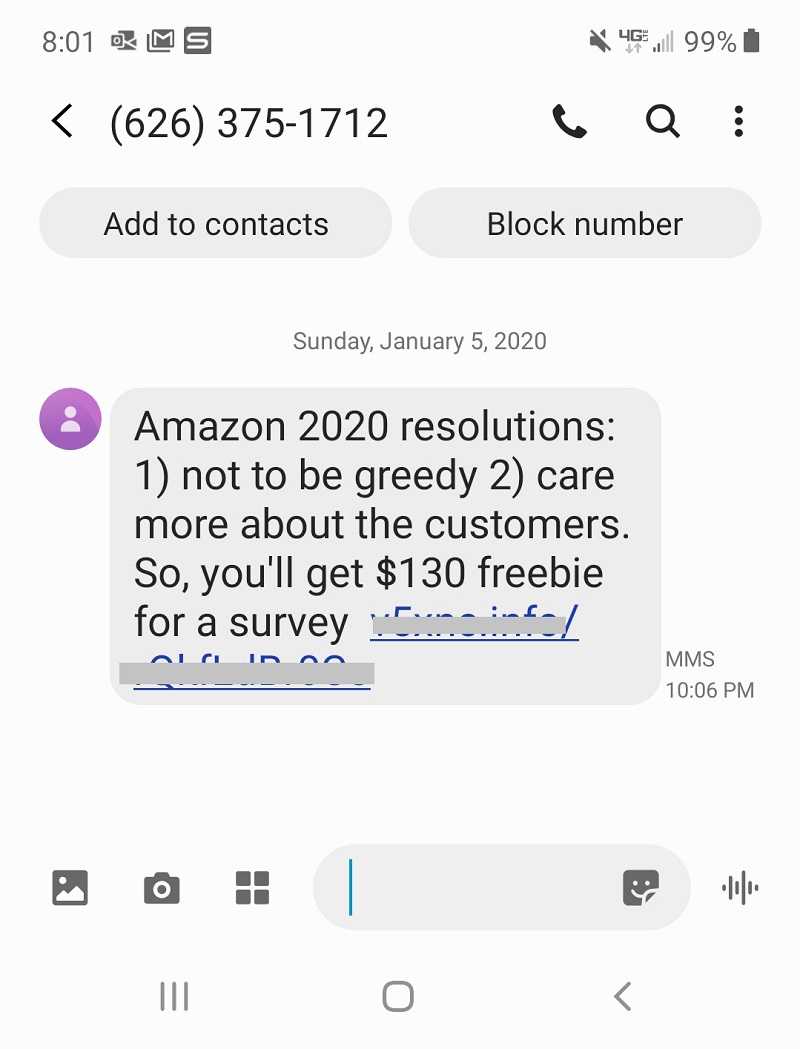 Smishing Smarts
Smishing Smarts
Not stopping at email and voice attacks, cybercriminals also send texts or “smishing” as a lure. Fraudsters send malicious text messages hoping to fool the recipient into responding. Text messages claiming you’ve won a prize or ask for sensitive data are tricks waiting for a reply. They can also have fake links to a website that’s designed to steal your data and funds. Suspicious texts are serious and a phone call to the true number of whom the text claims to be from can stop smishing in its tracks. Even better, just ignore it.