Multiple Bad Actors Actively Attempting To Exploit MobileIron Vulnerability
By: Jim Stickley and Tina Davis
January 30, 2021
In June 2020, MobileIron, a provider of mobile device management (MDM) systems, released security updates to address several vulnerabilities in their products. This included CVE-2020-15505, a remote code execution vulnerability, rated critical. It’s this particular issue that is catching attention of cybersecurity agencies and government institutions right now.
MDM systems allow system administrators to manage an organization’s mobile devices from a central server. While certainly convenient, it also makes them a valuable target for threat actors.
The U.S. Cybersecurity and Infrastructure Agency (CISA) is keenly aware that Advanced Persistent Threat (APT) nation-state groups and cyber criminals are now actively attempting to exploit this MDM vulnerability with intent to compromise the networks of organizations worldwide. The CISA has also noted that APTs are exploiting this vulnerability in combination with the Netlogon/Zerologon vulnerability CVE-2020-1472 from earlier this year using a single intrusion. It also noted that threat actors are exploiting both new and legacy vulnerabilities with this technique.
But good news! There is a patch for this vulnerability. Any organization that uses MDM should have applied it already. After all, it’s been out for a while now. If not, it’s a great time to get right on it. As with all patches, get them applied as soon as they are made available.
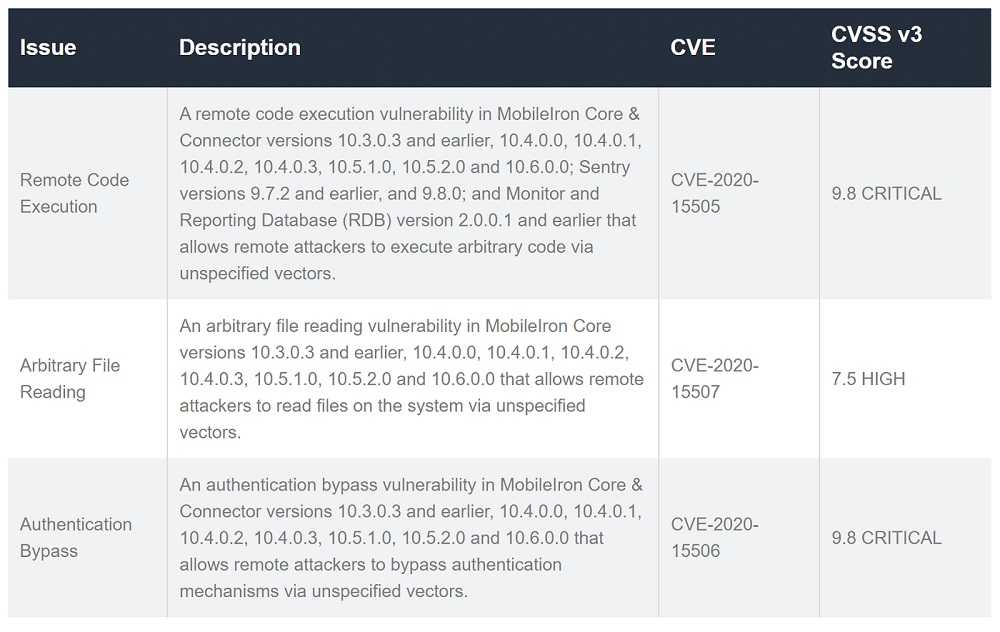
Available Patches:
- MobileIron Core & Enterprise Connector
Apply one of the following patches (v10.3.0.4, v10.4.0.4, v10.5.1.1, v10.5.2.1, v10.6.0.1) or update to a later version.
- MobileIron Sentry
Apply one of the following patches (v9.7.3, v9.8.1) or update to a later version.
- MobileIron Monitor and Reporting Database (RDB)
Apply the following patch (v2.0.0.2) or update to a later version.
- MobileIron Cloud
Status: Has been updated.
This critical vulnerability affects MobileIron Core and Connector products and could allow a remote attacker to execute arbitrary code on a system. The following versions are affected:
- 10.3.0.3 and earlier
- 10.4.0.0, 10.4.0.1, 10.4.0.2, 10.4.0.3, 10.5.1.0, 10.5.2.0 and 10.6.0.0
- Sentry versions 9.7.2 and earlier
- 9.8.0
- Monitor and Reporting Database (RDB) version 2.0.0.1 and earlier
A proof of concept exploit became available back September. Since then, both hostile state actors and cybercriminals have attempted to exploit this vulnerability. These actors typically scan victim networks to identify vulnerabilities, including this one. In some cases, when the latest updates are not installed, they have been able to successfully compromise systems.
The healthcare, local government, logistics, and legal sectors have all been targeted but others could also be, and likely are, affected. Don’t delay in getting this one patched.
It is also important for organizations using any of the affected versions to ensure they are following other best-practice cyber security advice, such as scanning their own networks and undertaking continual audits. This will help identify suspicious activity in the event that this vulnerability has already been exploited.