iPhone Espionage Attacks Using Zero-Click Pegasus Spyware
By: Jim Stickley and Tina Davis
March 18, 2021
For two months last year, three dozen international journalists suspected their iPhones were targeted with spyware, a type of espionage tool. When Citizen Lab researchers looked into their claims, they found zero-click spyware attacks had exploited a flaw in iPhone’s iMessage app and they were using Pegasus spyware to silently infect the journalists’ personal mobile devices. Their latest findings show a disturbing trend toward increased cyber espionage attacks on journalists and the media--and those attacks are continually more sophisticated and difficult to detect.
Citizen Lab discovered the iPhone attackers used Pegasus for their remote espionage, a notorious spyware created by the Israeli cyberarms firm, NSO Group. Founded in 2010, NSO Group created its flagship surveillance product and over time has sold or licensed it to governments, nation states, and other groups including those with a history of poor human rights records. They also believe the attackers may be linked to the United Arab Emirates and Saudi Arabia.

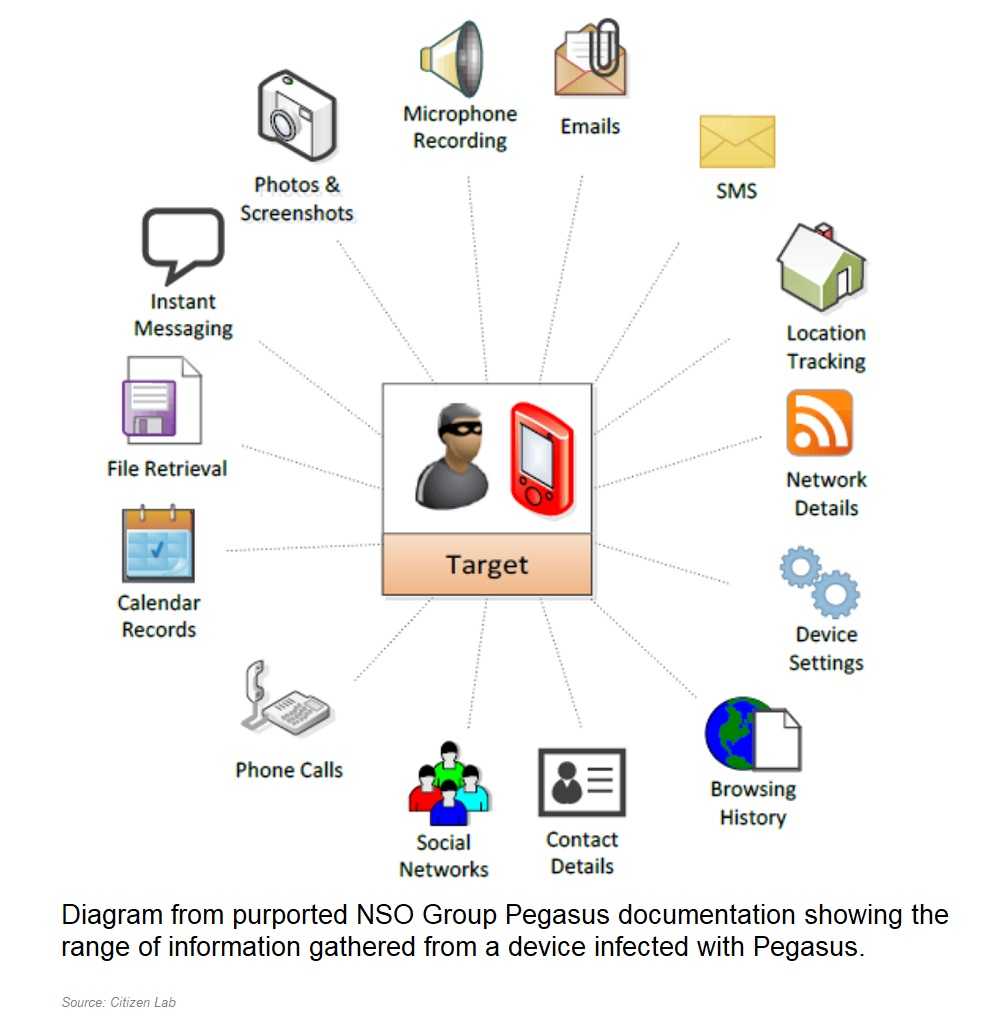
But it’s not just journalists that are targeted for these attacks. Pegasus gives remote attackers access to mobile devices and the information they contain; in this case the data is collected from iMessage. The iMessage app is preferred for global messaging because it uses the internet and there’s no need for an international data plan for phone calls and texting. Pegasus is able to collect sensitive insider information from iMessage targets, including background audio, phone conversations, passwords, stored credentials, GPS locations, and the ability to take pictures – everything necessary for successful, high-tech espionage exploits, whether government or private industry. NSO Group has since disputed the Citizen Lab report and some of its findings.
The zero-click element of Pegasus allows a system to be infected without any direct action by the user. Installing malware on a device often requires user action to work, such as clicking on an email phishing attachment that infects a system with malware when opened. In this latest case, the zero-click exploited the security flaw found in the iMessage app, including those iPhones used by the thirty-six journalists. The iMessage vulnerability was unknown to Apple at the time and they’ve since released a security patch for it in their iOS 14 rollout. Security experts note that updating to iOS 14 should be done immediately in order to fix the iMessage flaw; even if you don’t think you’re a target for this type of cybercrime.
In addition to Pegasus espionage tool being used against Apple’s iMessage, NSO Group is also currently embroiled in legal action by Facebook. The social media giant blames NSO Group for a similar zero-click espionage attack on their WhatsApp users. Facebook claims nearly 1,400 mobile devices were attacked by Pegasus spyware. According to them, over 100 human rights defenders and journalists were affected by the zero-click assaults. The company quickly responded to the spyware attacks by creating a security patch for the WhatsApp vulnerability, preventing further espionage using Pegasus from taking place.