Two factor authentication (2FA) or multifactor authentication (MFA) have always been encouraged by security professionals as a more secure way to keep your private information out of the hands of hackers. Many companies allow some type of MFA with their services, including Facebook, Google, and even the Nest thermometer. And it is indeed better than just using a username and password. But, it’s not the end all, be all in security. Google is reporting a big increase in the number of attacks that bypass MFA.
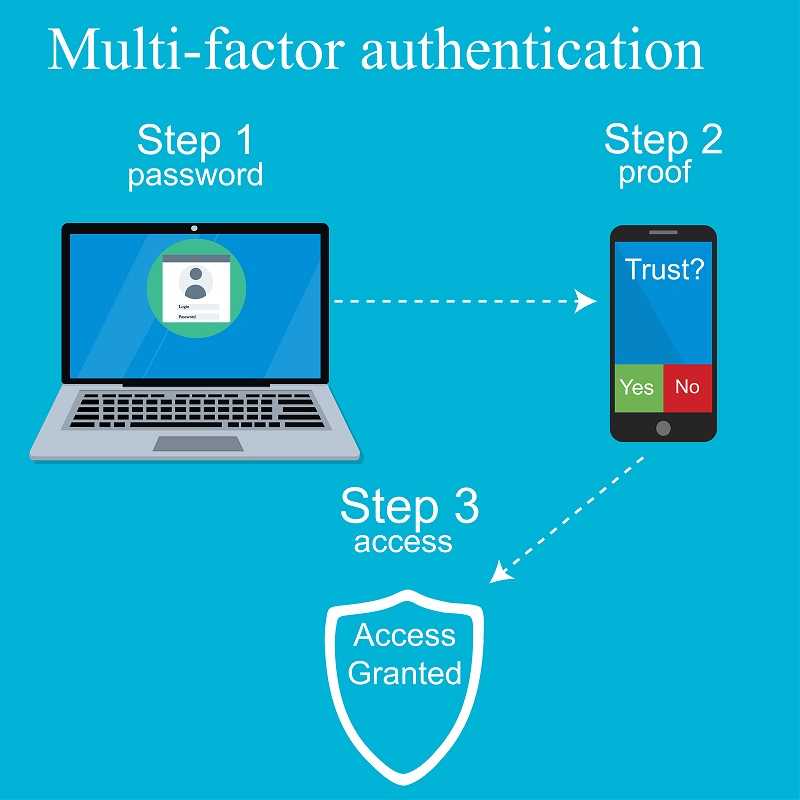 That said, it’s still far better to use some type of 2FA or MFA whenever it is offered. There are many ways to do this. Questions and answers sets, some type of fob that has randomly generated one-time codes, and text/SMS messages with a temporary code that may be valid as long as 30 seconds. This last one is what Google found to be used more often.
That said, it’s still far better to use some type of 2FA or MFA whenever it is offered. There are many ways to do this. Questions and answers sets, some type of fob that has randomly generated one-time codes, and text/SMS messages with a temporary code that may be valid as long as 30 seconds. This last one is what Google found to be used more often.
While you may think 30 seconds just isn’t long enough to do anything, turns out that it is. Google engineers said they have seen “phishing kits” that can steal the password and 2FA code as they type it into a fake email login page. They then get right to work and break into the account. Once they are in an email account, there are so many ways to steal information from the victims.
Remember that when you reset your password on your accounts, you often get an email letting you know it (or some other private information) was changed. If someone has your email password, he can ensure that you never get that notification.

 It is true that attackers also can grab your 2FA code if it’s sent via text or SMS too. Better safe than sorry and set your accounts to email AND text you when a change is made. That way, you change the odds of them pulling one over on you in your favor.
It is true that attackers also can grab your 2FA code if it’s sent via text or SMS too. Better safe than sorry and set your accounts to email AND text you when a change is made. That way, you change the odds of them pulling one over on you in your favor.
There is such a thing as SIM swapping too. That is when someone convinces someone else at your mobile phone company to switch your number to another phone. Unfortunately, this truly happens. However, the likelihood of someone getting the email and text notification deleted before you see it is low.
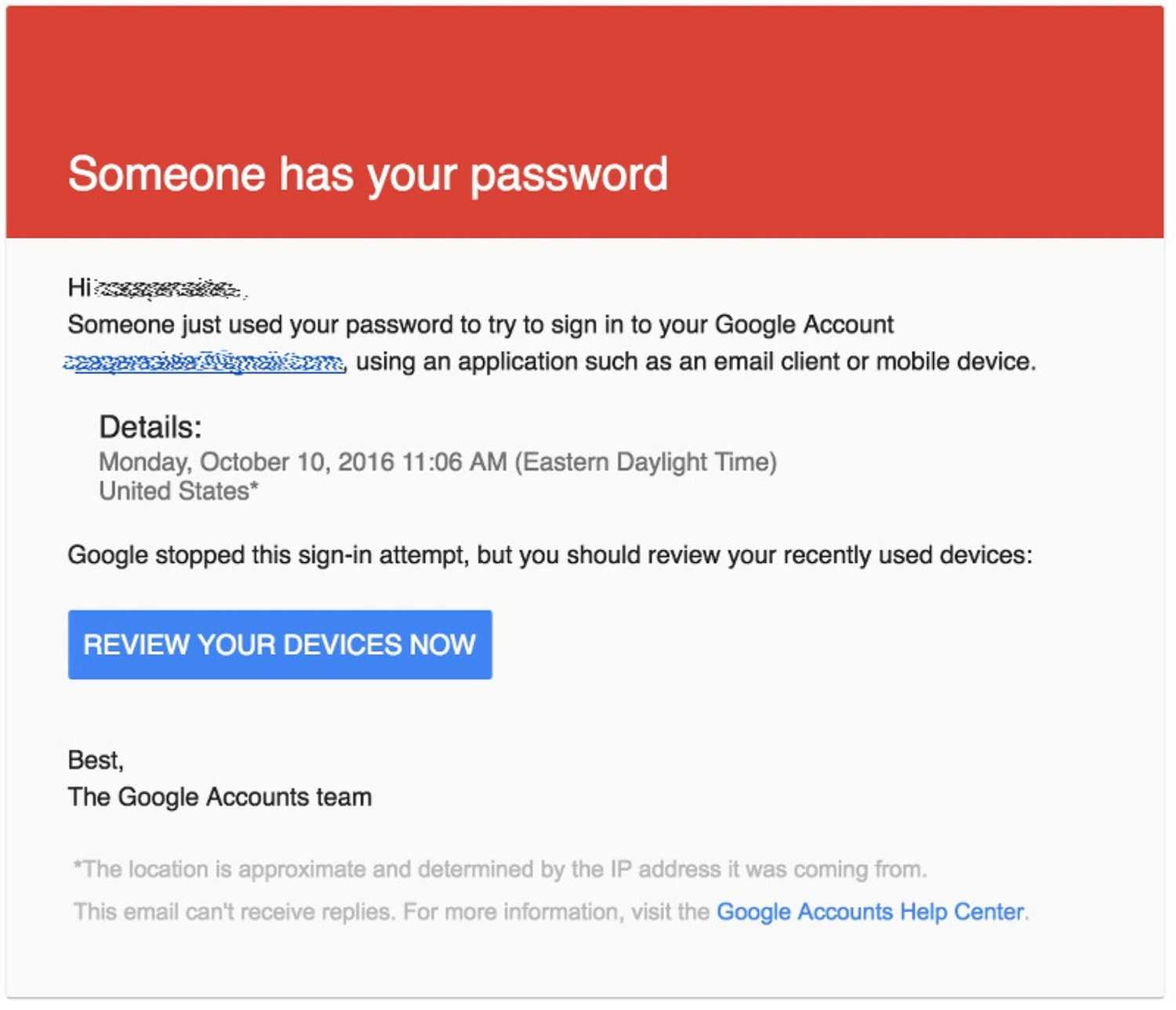
Google and other companies are making efforts to prevent these attacks by warning about login attempts from unfamiliar devices and even geographical locations. But those are not a 100% guarantee either.
While it’s not always the most convenient MFA option, hardware security keys have been found to be the best solution. These are tiny little items you can attach to a keychain that you put into your USB slot to authenticate to your accounts. However, while they don’t yet work with smartphones and tablets, they do work with laptops and any device with a USB slot.
In addition, always be on the lookout for phishing. No attachment or link is completely safe these days, regardless of format. So, if you aren’t expecting something, don’t click it. This applies whether it arrives in email or via text.